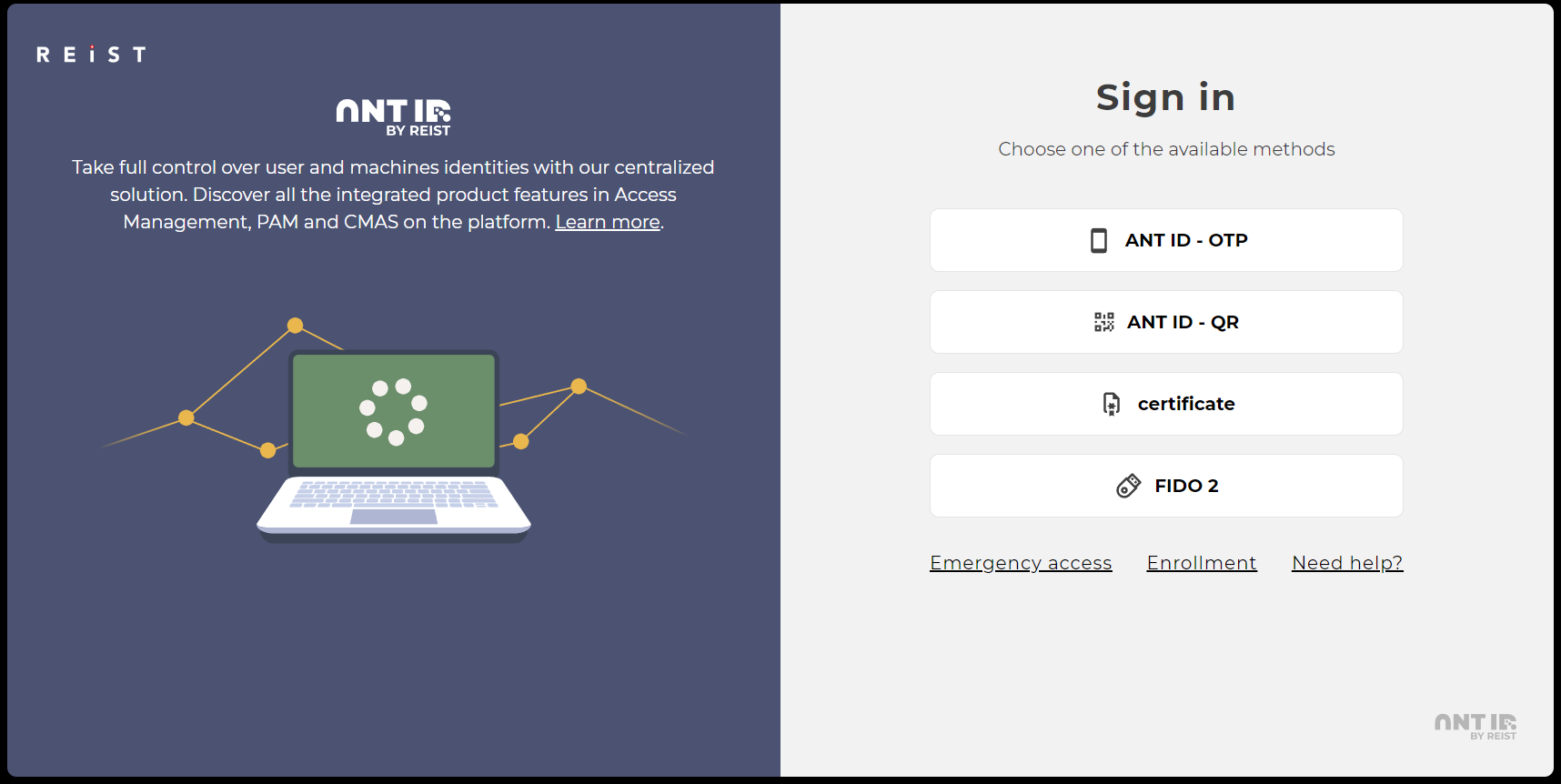
This is the login page. There are several ways to log in to the ANT ID system, which are described below. The login methods can be divided into groups:
|
Tokens are authentication methods using mostly one-time codes (OTP) as confirmation of the user's identity. This method can be used if the user has enrolled one of the tokens during the enrollment process, e.g. Virtual token, SMS, Email or Google authenticator and/or MS authenticator. For this method is depending of configuration sometimes possible to use it as password-less - you can insert OTP directly into the Password field. |
|
|
ANT ID - QR is a method using a token enrolled in ANT ID - OTP. The application can retrieve the displayed QR and confirm the user's identity via the stored token. |
|
|
Certificates can be used as verification of the user's identity if the user has a certificate issued by Reist that contains the stored identity of the user confirmed by Reist. |
|
|
FIDO2 is an open standard for authentication that allows two-factor authentication using specialized devices (e.g. USB tokens, NFC/Bluetooth devices) that can be used as a second factor without an additional password. The option is applicable for users who have a FIDO2 token enrolled in ANT ID. |
|
|
Emergency access is similar to tokens, therefore the same functionality is used. This is a situation where the user has requested an emergency access code for various reasons, where this code can be used instead of a code generated by an application such as google or ms authenticator. |
Note: login methods may vary depending on the configuration of each tenant.
Login via ANT ID - QR |
A prerequisite for logging in with ANT ID - OTP is ANT ID - OTP enrolled in Selfservice (or within Enrollment process) - see details here.
Login process |
|
1 |
On signing page choose ANT ID - QR option (button). |
|
|
2 |
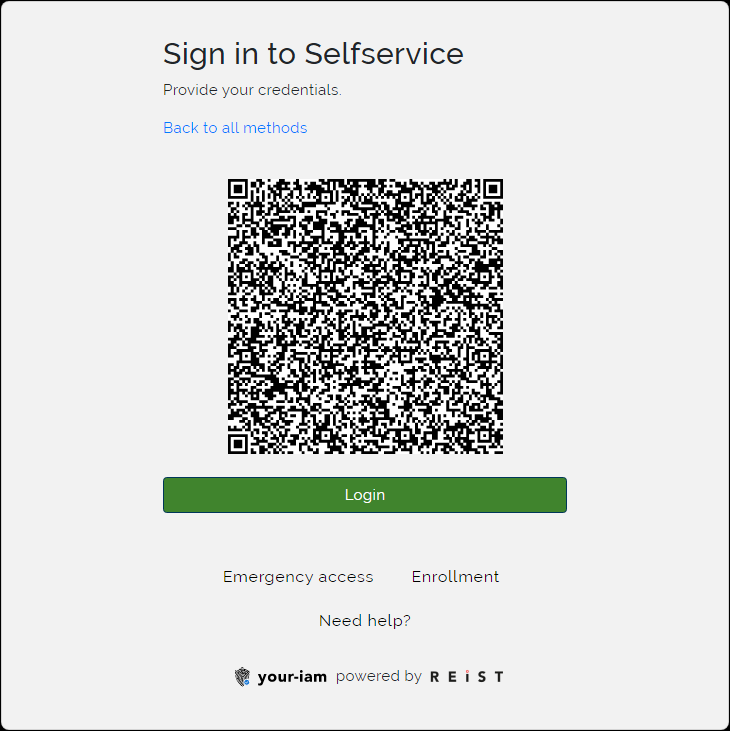
The application display QR code |
|
|
3 |
Scan the QR code with the ANT ID - OTP. If everything is correct, then the user will be logged into the ANT ID immediatelly. For the login on the mobile device where the ANT ID - OTP application is installed use the Login button - it will open the deeplink to the ANT ID - OTP app and the push notification will be created. Confirm the notification in the app and the access to ANT ID will be granted. |
Login via OTP |
A prerequisites for logging in with OTP (One Time Password):
- mobile application for management of tokens installed on the mobile device - see installation guide
- any of Virtual (SMS/Email) token, Google authenticator token or MS Authenticator token or any type of physical token enrolled in Selfservice (or within Enrollment process) - see details in the links.
Login process via username and password and Virtual token (SMS/Email) |
|
1 |
On signing page choose your-iam OTP option (button). |
|
|
2 |
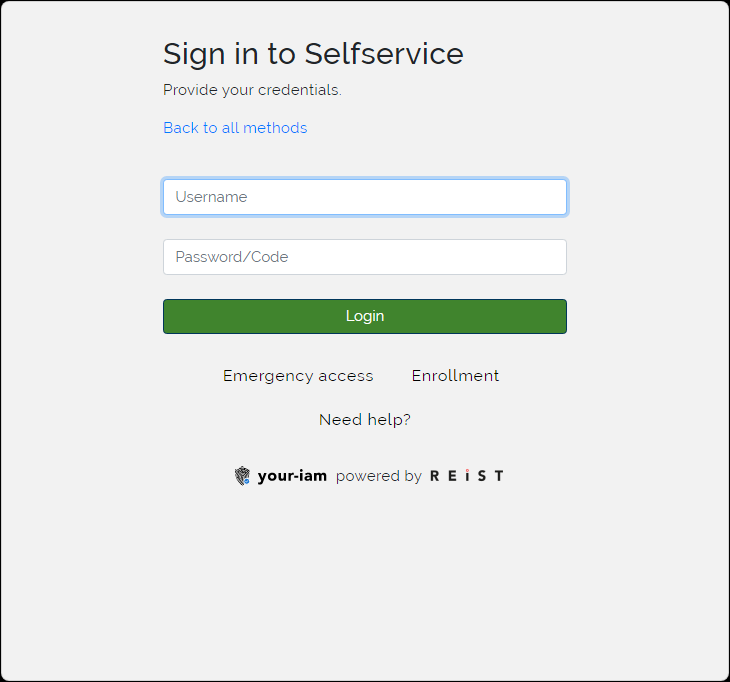
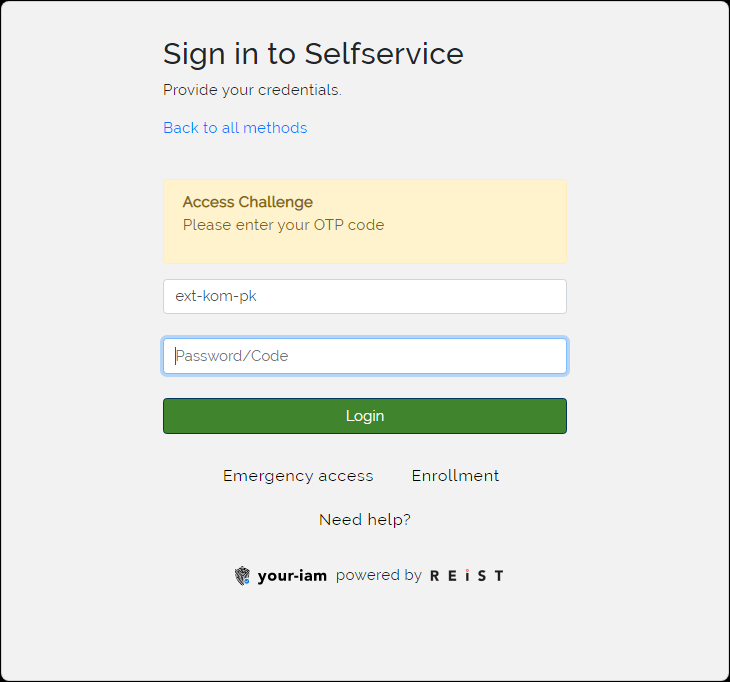
Fill Username and Password and press Login button. |
|
|
3 |
Insert OTP code received to the mobile phone or email address (depend on the type of enrolled token) or authenticator app and press Login button. If everything is correct, then the user will be logged into the ANT ID immediatelly. |
|
|
3a |
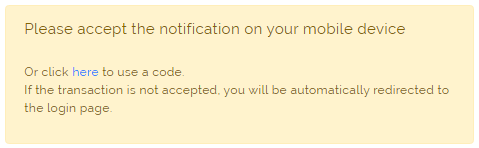
In case that user has also ANT ID - OTP app registered on mobile phone and ANT ID - OTP is enrolled then the push notification is send to the application (in the mobile phone) - if user confirms the notification on mobile phone and everything is correct, then the user will be logged into the ANT ID immediatelly. |
|
|
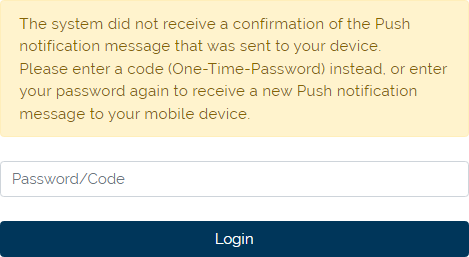
3b |
In case that push notification is not resolved in ANT ID - OTP by user then after some time the SMS with OTP is sent to user's mobile phone. Insert the OTP from SMS to the Password/Code cell and press Login button. If everything is correct, then the user will be logged into the ANT ID immediatelly. |
|
Login process via username and OTP from authenticator app |
|
1 |
On signing page choose your-iam OTP option (button). |
|
|
2 |
Fill Username and OTP code from your authenticator app and press Login button.
|
|
Login with certificate |
A prerequisites for logging in with certificate is to have relevant certificate installed in the computer - see details here.
Login process |
|
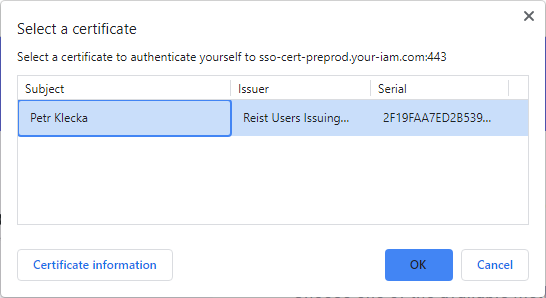
1 |
On signing page choose Certificate option (button). |
|
|
2 |
Select the relevant certificate and press OK button. If everything is correct, then the user will be logged into the ANT ID immediatelly. |
|
Login via FIDO2 device |
A prerequisite for logging in with FIDO2 is FIDO2 token enrolled in Selfservice (or within Enrollment process) - see details here.
Login process |
|
1 |
On signing page choose FIDO login option (button). |
|
|
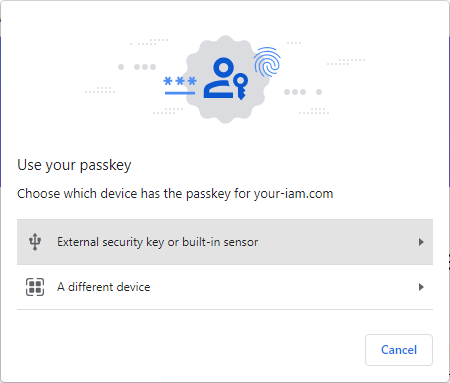
2 |
Insert FIDO2 token into USB port and select the External security key option. |
|
|
|
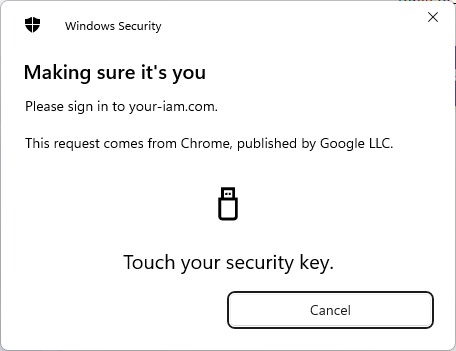
Browser will ask user to touch the FIDO2 token. In case of devices with fingerprint reader then touch the device with the correct finger. In case of PIN protected device the system request the PIN code. If everything is correct, then the user will be logged into the ANT ID immediatelly. |
|
Login via Emergency access code |
A prerequisite for logging in with Emergency access code is the generation of this code. There are two ways to obtain the code:
- In the Emergency access application after verifying the user's identity - see dectails here.
- By contacting an operator who can generate the code in the operations console
Note: The emergency code can be used to log in as a replacement for a standard OTP or as part of the approval process. Its validity is defined based on a template, BUT this code is deactivated when any of the following operations are performed:
- when the OTP address in the token changes (virtual, sms, email)
- the new token is enrolled
- the token is activated
Login process |
|
1 |
On signing page choose your-iam OTP option (button). |
|
|
2 |
Fill Username and Emergency access code generated in the Emergency access application and press Login button. If everything is correct, then the user will be logged into the ANT ID immediatelly.
|
|